PnP PowerShell and Multi-Factor Authentication
When you manage a Microsoft 365 Tenant, you often have to create accounts with some privileges/roles on the same Tenant. For example, an account as SharePoint Online administrator 🙄.
Once you have created a Microsoft 365 Tenant for your company, some rules of governance have to be respected and mainly those security ones. One of them, which is a Best Practice, consists of activating the MFA (Multi-Factor Authentication) on accounts that have a specific role(s) (especially if it is a service account).
You can configure the MFA to use text messages or mobile applications. I will show you how to configure it, expose you to the side effects of your PowerShell scripts, and how to deal with it.
[info]Important
In this use case, it is an account with the SharePoint administrator role.
Why enable MFA?
The main reason is "increase security"! Even if someone finds your password, he won't be able to connect to your account without validation or a code generated by your smartphone. And for other reasons like:
- Users cannot use App Password (I'll explain to you below what it is exactly) to connect the Office Portal
- App Password never expires (you can set "never expire password" for a specific account but it is not obvious to manage this kind of accounts and it is not recommended)
- Users can change their password and the App Password stays the same
- You can generate several App Passwords (I don't know if this case is really interesting but you can 😉)
- You can revoke all App Password in one shot
- For security reasons, all accounts with admin role(s) should have MFA activated (especially for the Global Admin role)
- If an enterprise wishes to have a good score on Microsoft Secure Score, enabling MFA is recommended (CSA CCM301, Control DSI-02, FedRAMP Moderate, Control IA-3, GDPR, etc.)
There are still other differences/reasons, but here are the ones I expose to my customers and also why I generally advise activating the MFA.
PowerShell script without MFA
In this example, we'll use the PnP PowerShell Framework to connect and count the number of SharePoint site collections of Tenant.
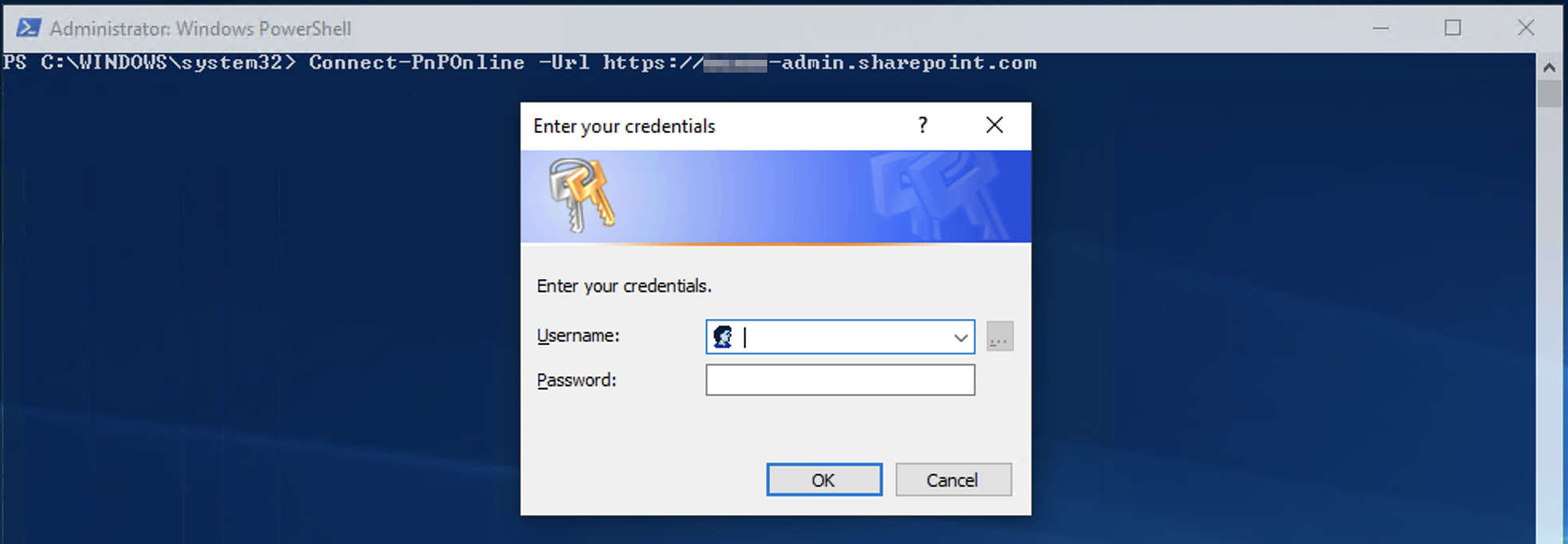
- From the PowerShell console, use the connect cmdlet :
Connect-PnPOnline -Url https://yourdomain-admin.sharepoint.com
- A Windows prompt should appear. Fill out login ([email protected]) and password
- Now, to show all SharePoint site collections, use the below cmdlet :
(Get-PnPTenantSite).Count
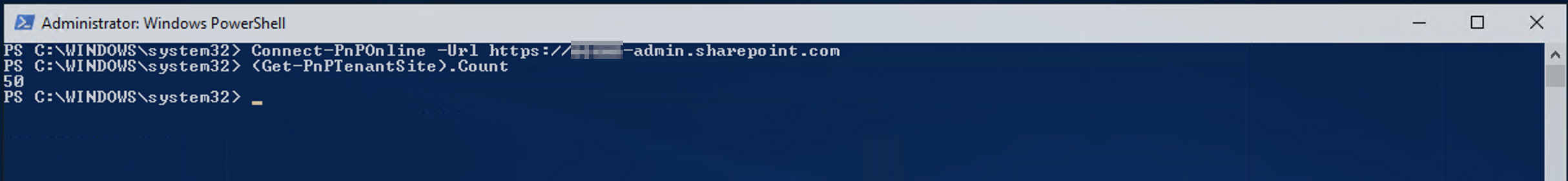
It works! 💪🏻
Configure MFA on an account
Prerequisites
- Connect to Microsoft 365 Central Admin with an account with sufficient rights
- A smartphone
- If you haven't already installed
Microsoft Authenticator Appon your device, you can do it from here:

Configuration
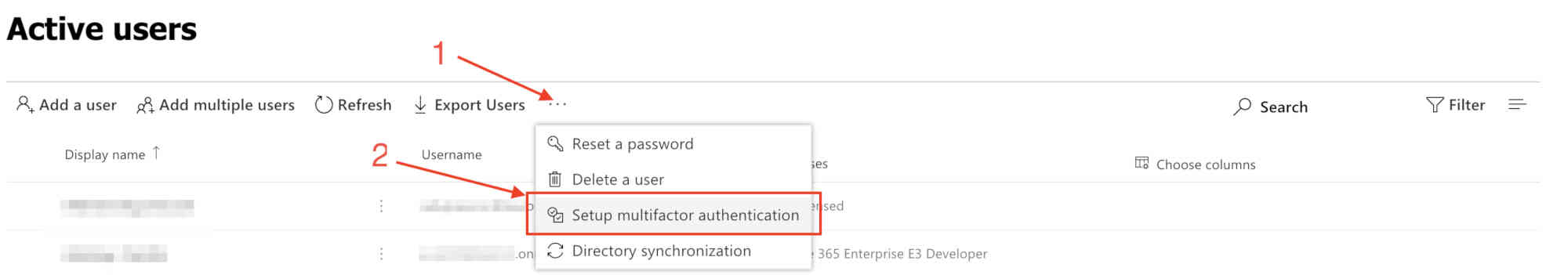
- From the Microsoft Central Admin, go to Active users
- Click on the ellipsis located at the top bar and click on Setup multifactor authentication
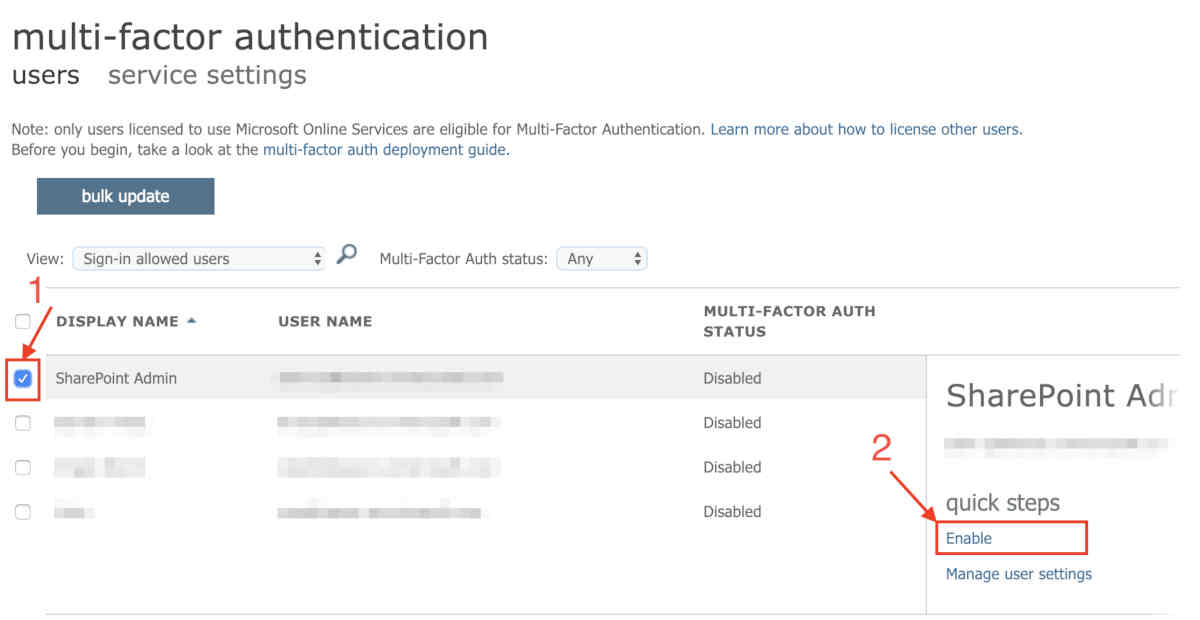
- From the Multi-factor authentication page, select the target account that you want to enable MFA
- To the right side, click on Enable
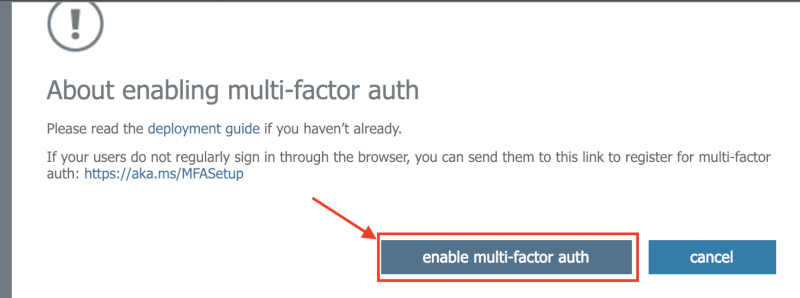
- From the dialog that will appear, click on enable multi-factor auth
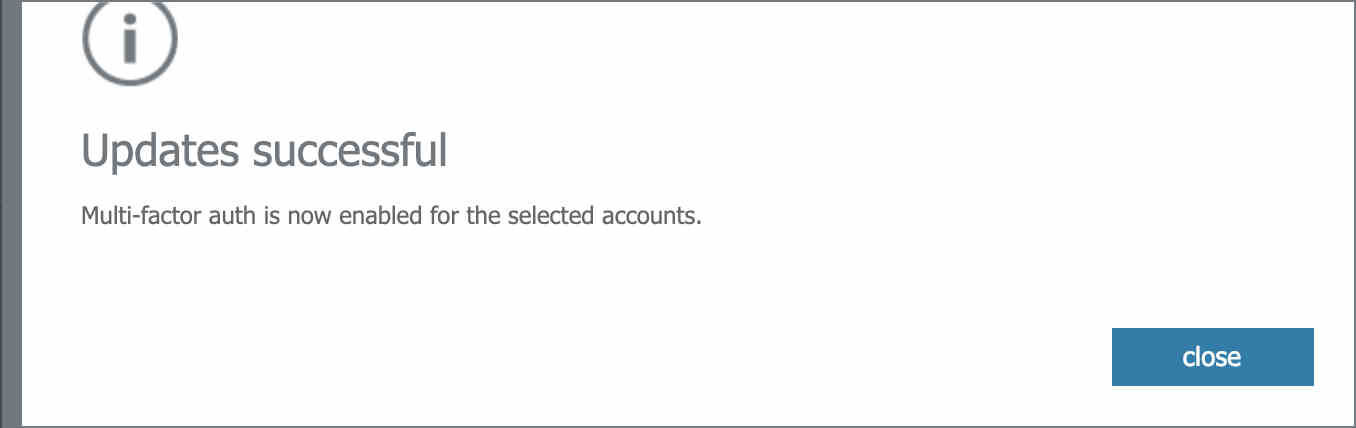
- From the successful message dialog, click on close
- Logout the current user or change browser
- Log in with the target account that enabled MFA on it
- Configure the Mobile App Authenticator
- Generate your first App Password and save it somewhere
[note]Note
Here, the link to access directly to the App Password manager: https://account.activedirectory.windowsazure.com/AppPasswords.aspx
That's done! 😅
PowerShell script with MFA
- From a new PowerShell console, use the connect cmdlet :
Connect-PnPOnline -Url https://yourdomain-admin.sharepoint.com
- A Windows prompt should appear. Fill out login ([email protected]) and password (like previously). But this time, after authentication, you should have an error message like this one :
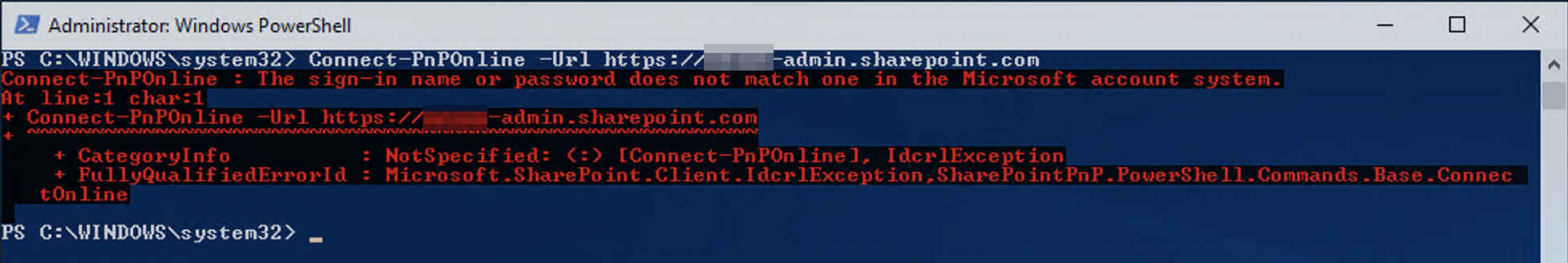
- Now, try again, but this time, use the App Password instead of user password
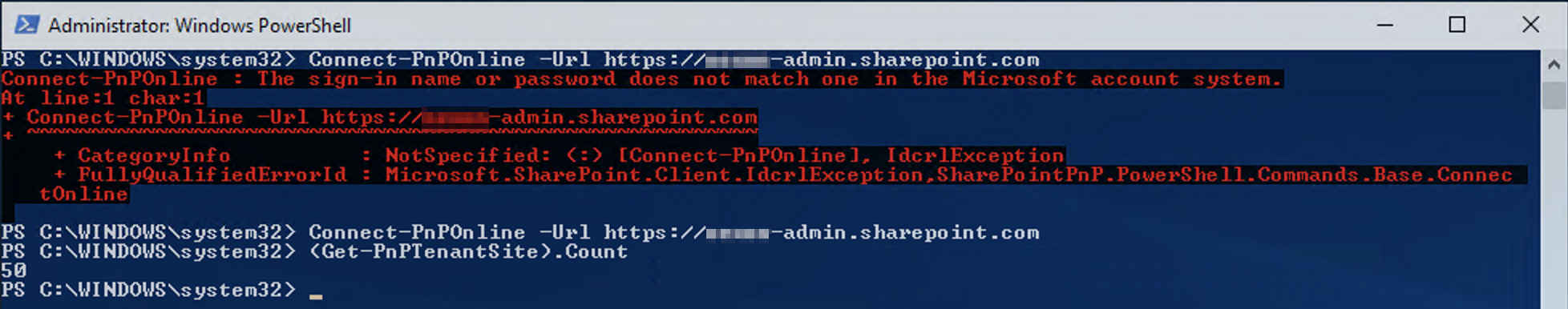
It works again! 🤗 pfiou
It still does not work!
Microsoft provides several methods of authentication and it is possible to block Legacy authentication.
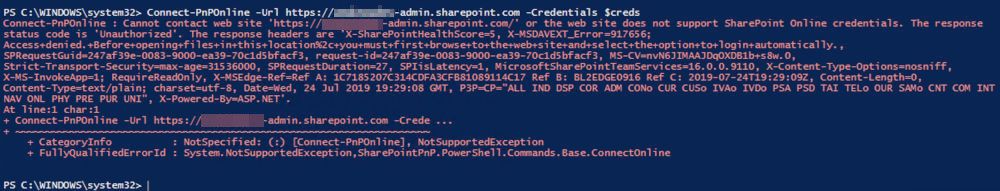
You can enable the Legacy Authentication with the following cmdlet:
Connect-SPOService -Url https://contoso-admin.sharepoint.com
Set-SPOTenant -LegacyAuthProtocolsEnabled $true[note]Note
You will have to wait a couple of times before the changes take effect... Microsoft announces 24 hours, but in my cases, it never took more than 15 minutes.
[note]Note
In other use cases, MFA and App Password will not work, especially if you're using Microsoft Graph API. Other ways are available to connect to Microsoft 365 services like certificate or App Client/ID.
Hoping this post will help you 😉